I'm posting this on behalf of PurpleFreeze, Demoria's former lead developer of DCE (Demoria Custom Engine)
Hey everybody this is PurpleFreeze (AKA Alex H) Demoria and Chaotic United are safe for the meantime. 2 weeks ago last Sunday, there were a couple staff members and player's on when suddenly connection for the server just dropped. That was because the server's ethernet was overloaded and made Superdoctor 5 (Our hardware analysis program) disable ethernet as we had set it to that option to prevent the ethernet adapter from shorting out from receiving too much data.
You might be asking, how did someone figure out a server that barely anybody from the public would know about? Let alone the port number's that Demoria uses.
It is very easy to find out what ports are open on somones network with a quick scan and a program that can send a large amount of packets to take it down. Originally, we ran Demoria with no firewall because it was easier to run. But now we see that people want to put an end to our ambitions. So Michael spent 3 hours configuring a firewall that separate's all ethernet connections to a certain speed and filter's packet's. The firewall has worked perfectly since then.
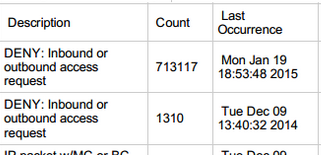
Their decision to use a DDoS attack is a good sign. We've repeatedly received various threats from these individuals about breaking into the servers in some manner or another, at some certain time, for them to do some certain damage. Each time, these threats have proven to be completely false. Reverting to a DDoS attack is comparatively far less harmful and extremely unsophisticated, so this can be taken as a sign that they're ragequitting the "subvert our actual security" plan.
Michael and I have deliberately avoided working with the server to put our next plan into action
The impression that this guy is trying to make is that he can just waltz into anyone's account whenever he wants and delete everything. This is not the case: the users affected all had weak enough passwords that he could crack them after about 60 guesses. Additionally, we have account recovery features that we have used to restore the items and return them to their rightful owners.
Now you may be thinking that 60 guesses is a lot. Most of these things are not done by hand, but rather through a simple program or script to try passwords from a pre-defined list and record the successful ones. This is where we must admit a small mistake on our part: the industry-standard way to protect against this is to put a rate limit on how quickly a given computer may attempt logging in. When we designed our accounts database, we were only focused on the (extremely small) alpha test, and features like that didn't get implemented yet.
We finally implemented rate-limiting by returning fake results when a dictionary attack is detected, which interestingly enough caused our attacker to come storming into our IRC and immediately demand to speak to a developer
I'm really not entirely sure where his sense of self-entitlement comes from, but I suspect he was frustrated by the numerous fake entries he ended up with thwarting his plans.
To better understand his attack, we allowed him to continue under careful control and monitoring - a technique known in the industry as "honeypotting." A honeypot is essentially an isolated sandbox that you can put naughty kids like this into to keep them away from "real" information and better understand their behavior.
That is why exactly we "intentionally made the database's go into DIRM mode (Dictionary Intrustion Recovery Measures)
This stop's all information from being written but instead it was marked as read-only
Nothing of value was lost, but it was showed to him that he is not welcome on our server's and he was trolled and that he is wasting his time.
Clues Left:
- The first character he intruded was named Hocesta venatus which translates into This is a Game.
- He was moved to an non-existant zone in the game called Ageiterum, which means Try Again?
- Items were unable to be used and he would constantly be moved to an area that he was at before, as if he was lagging and hurting our servers. LOL No
On that last point: As he's already been shut out of the system, and working from a list of compromised accounts from Monday.
Finally I ran a security audit on all of our systems. This involves double-checking the logs, configuration, and behavior of each node to ensure that nothing has been comporomised and nothing has been accidentally misconfigured. I'm pleased to report that there is still no evidence that our database is (or ever was) accessible to anyone else (and if it was, why go through all this trouble? Just rename all the Characters to something offensive).
Thanks for reading and bearing through with us as we worked this out,
Sincerely,
PurpleFreeze

